Introduction
Achieving NIS 2 compliance requires analysis of regulatory requirements on a local level. However, across various geographies, risk analysis stands out as a particularly critical component.
Under NIS 2, risk analysis is not just another compliance requirement; it is a foundational element in shaping an organization’s cybersecurity ecosystem to meet NIS 2 standards. The results of a thorough risk analysis should guide decisions at the security architecture level, influencing investments in tools and the processes implemented.
Risk analysis will play a central role in NIS 2 audits. Auditors won’t simply verify the existence of a risk analysis—they will also demand evidence that it has led to the implementation of appropriate safeguards.
Moreover, proper risk analysis can be instrumental in root cause analysis during incident investigations, helping to determine whether a flawed or absent risk analysis contributed to the incident.
Because of its importance, risk analysis should be one of the first steps in the journey toward NIS 2 compliance. It serves as a roadmap for other decisions and actions supporting compliance.
Risk Analysis: The Foundation For Driving Changes In Policies, Processes, And Security Architecture
Organizations can use a risk matrix to evaluate specific risks by assessing their likelihood and potential impact.
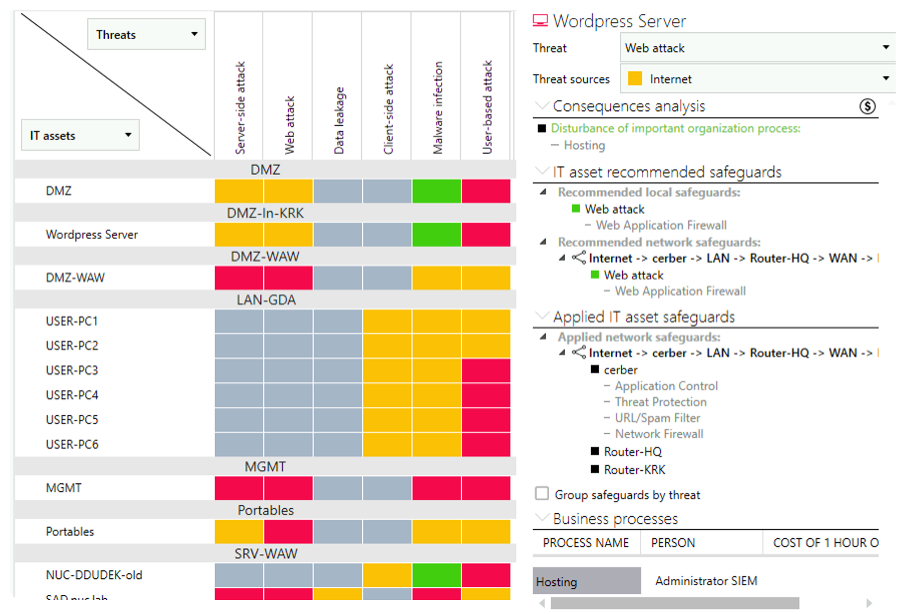
SecureVisio's risk matrix
Risk analysis should address risks related to actual processes, existing assets, safeguards, policies, and procedures. When a risk is identified, the organization must evaluate its impact, likelihood, and overall risk level. This leads to actionable responses that mitigate potential consequences.
Below is an outline of the approach to analyzing individual risks (in brief):
- Risk Identification: Risk of data confidentiality breaches by unauthorized employees
Analysis: Probability, impact, risk level, etc.
Example response: Update information security policies, staff training, or revise data access controls. - Risk Identification: Having an unsecured web server
Analysis: Probability, impact, risk level, etc.
Example response: Implement a Web Application Firewall (WAF). - Risk Identification: Lack of regular backups
Analysis: Probability, impact, risk level, etc.
Response: Implement backup policies and tools, test data recovery processes, etc. - Risk Identification: Risk of unauthorized access to billing systems
Analysis: Probability, impact, risk level, etc.
Response: Implement Multi-Factor Authentication (MFA).
And so on.
Risk Analysis: A Pillar Of Nis 2 Compliance
Under NIS 2, risk analysis is not merely a documentation exercise—it’s a process that must actively shape security decisions. Auditors will evaluate how effectively risk analysis impacts policies, processes, and architecture.
Key areas of focus for auditors include:
- Documentation of Risk Analysis:
Auditors will examine the identification and prioritization of threats and vulnerabilities, alongside critical risk levels requiring action. Risks must encompass a broad spectrum, including cybersecurity threats, physical risks and industry-specific concerns. Organizations must also demonstrate clear prioritization of risks based on their severity and likelihood.- Link Between Risks and Protective Measures:
Auditors will assess whether the organization has implemented appropriate controls for identified risks. Each control must be justified with documentation showing its relevance and effectiveness in addressing specific risks.Risk profiles and protective measures should adapt to new information, threats, and organizational changes, including:
- Internal developments (e.g., new business segments or IT systems).
- External factors (e.g., changes in laws, evolving security threats, and advanced attack techniques).
Organizations should also track key performance indicators (KPIs) to evaluate the effectiveness of their risk management practices, ensuring continuous improvement.
By embedding risk analysis into the core of their compliance efforts, organizations not only meet NIS 2 requirements but also strengthen their overall cybersecurity resilience.
Securevisio Provides Platform And Experts To Perform Risk Analysis
Risk analysis serves as the cornerstone of NIS 2 compliance. Engaging experts during this process—particularly at the initial stages—can help establish solid foundations for ongoing risk assessment, which can then be maintained by the organization as changes occur.
As SecureVisio, we provide both experts skilled in risk analysis and our automated platform providing up-to-date risk levels and safeguard recommendations.
At SecureVisio, we offer both a team of skilled experts and an automated platform designed to deliver:
- Up-to-date risk levels
- Tailored safeguard recommendations
How Risk Management Works in SecureVisio
- Comprehensive Infrastructure Mapping
- Our agent scans your infrastructure and creates a Configuration Management Database (CMDB), storing critical details about IT components.
- Automated Risk Assessment
- Our tools evaluate specific assets, identifying the likelihood of particular attacks, recommending safeguards, and assessing the consequences of breaches.
- Business Impact Analysis (BIA)
- Our BIA functionality delivers information on the business processes at risk, empowering better decision-making.
- SIEM Integration
- Risk outputs enhance other platform functionalities, including:
- Attack path creation for events and incidents.
- Real-time risk level updates for incidents.
- Threat prioritization using an internal risk scoring mechanism.
- Risk outputs enhance other platform functionalities, including:
- Enhanced Visibility with CTI and Vulnerability Scanners
- Integration with Cyber Threat Intelligence (CTI) platforms and vulnerability scanners provides a more comprehensive view of real risks.
Expertise Beyond Technology
We also offer specialized expert support, including:
- Developing risk assessment methodologies and techniques
- Conducting threat modeling – including developing potential attack scenarios on the organization by identifying possible attack techniques within the client’s IT environment (based on the MITRE ATT&CK framework)
- Supporting organizations in conducting their own risk assessments (consultations) or optionally performing the risk assessment process
With SecureVisio, you’ll have the tools and expertise needed to make risk analysis the backbone of your NIS 2 compliance journey.
Explore SecureVisio’s risk analysis platform and collaborate with experts who bring extensive experience in risk assessment. Streamline your NIS 2 compliance journey with our comprehensive solutions.