Early detection and mitigation of vulnerabilities in IT systems processing personal data, financial data, and other sensitive data as well as those used for important business processes are the priority for cybersecurity. If these vulnerabilities were to be exploited, your organization could suffer considerable losses. SecureVisio uses a variety of scanners and CVE feeds to automatically detect vulnerabilities in IT and OT environments. The Vulnerability Assessment Scheduler defines the automated vulnerability scanning schedule as well as the list of tools used.
Compatible with both commercial canners and open-source tools, SecureVisio offers independence and flexibility in vulnerability management operations.
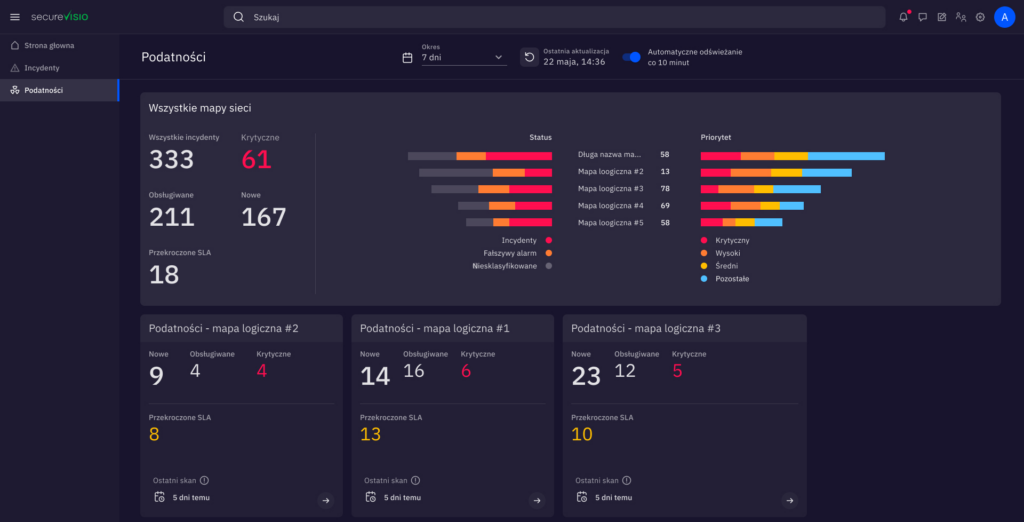
When security staff are faced with a large number of vulnerabilities, business-critical issues are often not identified until visible security breaches occur. SecureVisio solves this by immediately notifying IT security staff of new business-critical vulnerabilities. All discovered vulnerabilities are automatically prioritized based on CVSS Score, technical severity, and potential business impact. The potential damage that could result from a cyberattack is estimated automatically for all vulnerabilities – something no other solution can offer.
SecureVisio provides an interactive panel displaying vulnerability data collected from a wide range of tools. These data are then enriched with relevant information (either automatically or on demand), such as contact data for systems administrators and management. Workflow tools define tasks and processes, including for vulnerability analysis and response. This keeps everything running smoothly and allows you to track status, SLA, and useful metrics such as average resolution time for vulnerabilities of a particular business priority. Playbooks offer predefined actions to automate vulnerability analysis, response, and management processes.
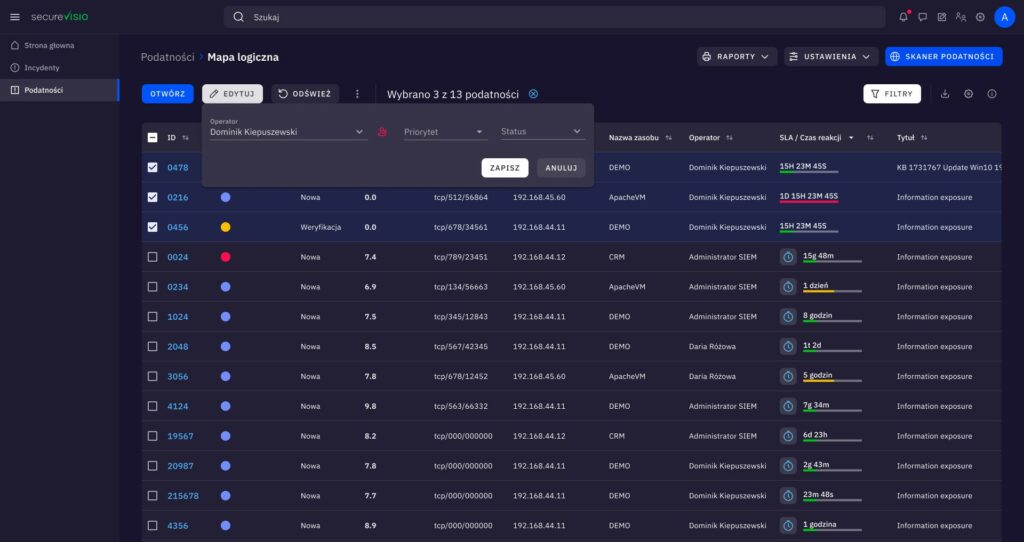
SecureVisio addresses one of the most difficult problems associated with vulnerability management: what should you do if a patch for a critical vulnerability cannot be installed? How long can the organization take the risk? In these cases, we can use IPS or WAF to deploy virtual patches that make it difficult for cybercriminals to exploit potential vulnerabilities. SecureVisio uses the Network Map to visualize all possible attack vectors; based on this information, you can quickly identify the appropriate safeguards, including virtual patches.

