Origins of SIEM
SIEM officially entered the cybersecurity scene in 2005, first defined in a Gartner report, though the roots of Security Information Management (SIM) and Security Event Management (SEM) tools trace back well before that.
The early promise of SIEM technology was to centralize log data collection across organizations while providing the workflows and insights necessary to identify, categorize, and analyze cybersecurity incidents and events.
In the early 2000s, SIEM solutions were expected to gather and prioritize security alerts generated by tools like firewalls and antivirus solutions effectively. However, after two decades, limitations of traditional SIEM tools have become apparent.
SOC teams, third-party experts, and analysts have increasingly advocated for change.
What Happened Then?
Since 2005, we’ve experienced a technology tsunami—mobile, cloud, IoT, OT, Big Data, GenAI, and more. Changes in infrastructure, business models, security tools (endpoint, network, IAM), regulations, attack surfaces and the sophistication of threats have transformed the cybersecurity landscape. These advancements have exposed the inherent limitations of many SIEM tools.
Many threats fail to trigger alerts, while security teams struggle to continuously update broken detection rules as environments evolve. SOC teams are still overwhelmed with alerts — according to IDC, up to 30% of alerts are ignored or improperly handled.
There is still so much focus on detection and reaction, while basic prevention measures, attack path discovery, and proactive defenses are overlooked — only 17% of organizations can clearly identify and inventory a majority of their assets.
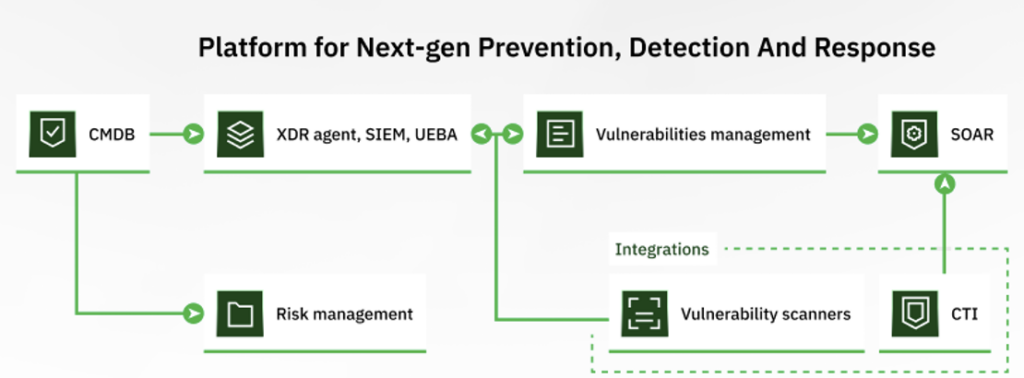
These Insights Shaped the SecureVisio Platform
These deep-rooted issues extend beyond SIEM technology itself, but we had a number of assumptions when developing SecureVisio that allowed us to combat some of the challenges.
We created one platform that on top of SIEM, SOAR, and UEBA features brings number of unique capabilities such as risk-based threat prioritization, a cyber asset database, BIA (Business Impact Analysis), attack path mapping, and much more.
Our assumption no. 1 – Provide Real-Time, Risk-Based Threat Prioritization
Traditional SIEM tools focus heavily on analytics but often fail to adjust to the specific context of an organization. This means companies of all sizes and complexities receive the same standardized solution.
Our Approach:
SecureVisio provides real-time risk scoring for every event, incident, and vulnerability, giving human analysts entry-level visibility into real risks faced by their organization. We prioritize vulnerabilities and incidents by factoring in:
- Existing security measures (e.g., applied WAF)
- Exposure of the affected asset (e.g., critical server)
- Incident-specific risks
- Cyber asset and business process criticality
- Threat intelligence feeds
- And many more
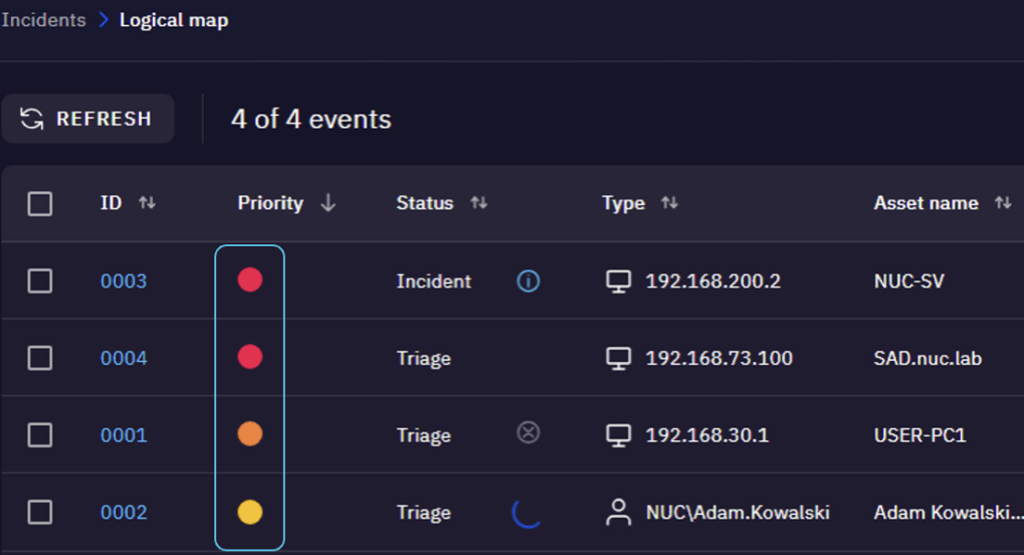
This approach eliminates the noise of endless alerts. Analysts can focus on real threats, drill down into risks, and understand the broader impact — such as affected business processes.
Our assumption no. 2 – Deliver Contextual Enrichment in Real-Time
Our SIEM solution provides all necessary capabilities for discovery, detection, and analysis of threats, including:
- Data ingestion and storage (in the case of SecureVisio via syslog, API, built-in XDR agents, etc.)
- Real-time event correlation, monitoring, and analytics
- Compliance and reporting
- Dashboards
- Third-party integrations (e.g., CTI feeds)
- And many others
But we go further than this. SecureVisio adds a CMDB-powered contextual layer. With SecureVisio you can:
- Trace incidents and vulnerabilities back to specific cyber assets (e.g., VMs, physical servers, routers)
- Understand asset criticality, ownership, and dependencies in your network
- Identify security zones (i.a. LAN, WLAN), asset locations, and associated business processes
Our platform even maps potential attack paths, indicating how incidents might spread laterally across your environment.
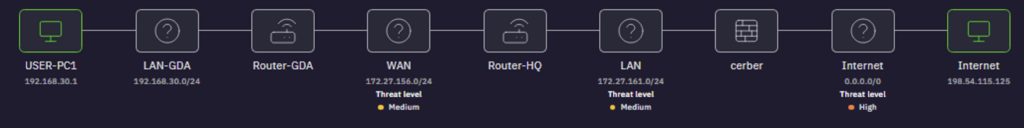
Our assumption no. 3 – Better Prevention and Proactivity Will Impact Threat Detection
Organizations with strong security postures have fewer entry points, greater awareness of real risks, security zones, and better processes — resulting in more efficient threat detection and response.
For this reason, we provide a CMDB database and risk matrix so that security teams can continuously study their infrastructure, see current risks, and receive real-time recommendations to minimize risk levels.
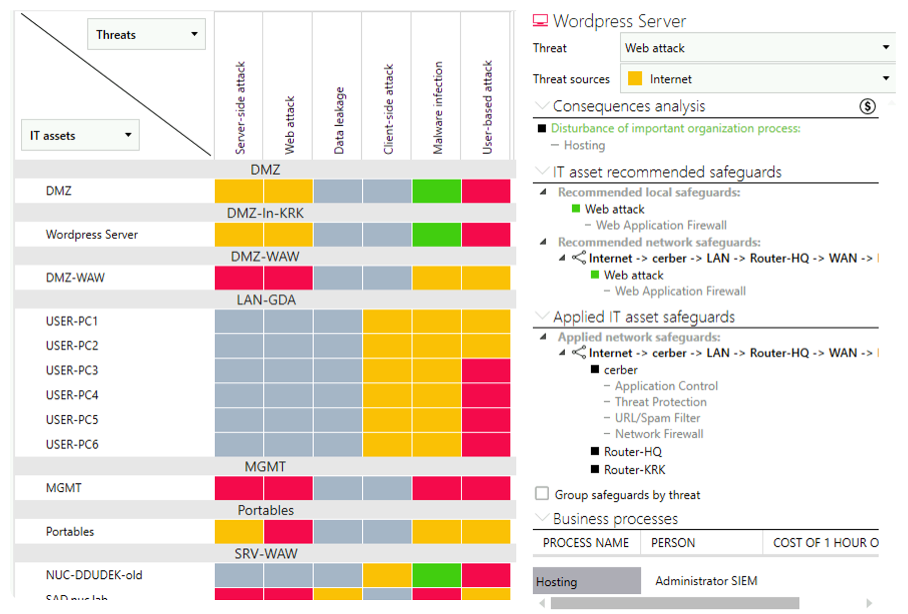
With our safeguard recommendations, you will invest in the right technologies and develop the necessary processes finely tuned to the organization’s environment. This allows security teams to focus on real threats and reduce alert noise from SIEM.
Our internal Business Impact Analysis (BIA) solution links attack vectors to real-life business implications, providing security teams with actionable insights.