Introduction
Attack Path Analysis is a continuous process of discovering visualizing and analysing potential routes attackers could exploit to breach IT systems and infiltrate networks.
Several key developments in the cybersecurity landscape have converged to make Attack Path Analysis not just valuable, but essential:
- Prevention gaps arise from teams focus on detection and reaction
- Traditional periodic assessments fail to address dynamic attack surfaces
- Siloed security tools miss critical path combinations from vulnerabilities and privileges
- Infrastructure complexity requires comprehensive path understanding
Well-structured Attack Path Mapping address these challenges by continuous discovery and analysis of assets, mapping dependencies and interactions, as well as analyzing vulnerabilities to understand pathways that threat actors might choose.
In this article, we will present key elements of attack path mapping and techniques that provide comprehensive and up-to-date information about potential threats.
Attack Vectors vs Attack Surface vs Attack Paths
Before diving into attack path mapping, it's crucial to understand the key differences between related security concepts:
- Attack Vectors: Specific methods or techniques that attackers use (e.g., SQL injection or compromised credentials)
- Attack Surface: The total sum of all possible attack vectors
- Attack Paths: The complete routes an attacker could take through your infrastructure, combining multiple actions and moving laterally to reach their target
Key components of Attack Path Analysis
Structuring an Attack Path Analysis program that analyzes all pathways, scores risks, and provides actionable responses requires:
- Data collection (assets, their dependencies, and information from cybersecurity tools – logs, vulnerabilities, etc.)
- Identification of how threat actors gain initial access and their lateral movements
- Risk scoring for attack paths and proposed remediation efforts
Data collection
To understand attack paths, you need a clear picture of your assets. This includes all devices and systems within your network, cloud resources and services, endpoints, and other assets (like IoT devices).
You need to understand their security controls, configurations, dependencies, access levels, and more.
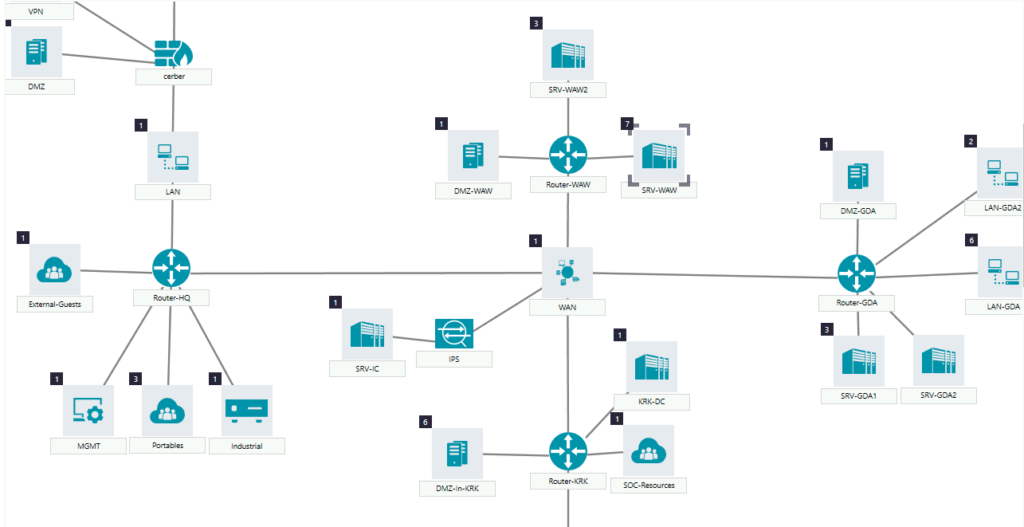
SecureVisio’s CMDB solution provides visual representations of potential attack paths and the relationships between assets
For real-time analysis, we need access to various data such as network traffic, authentication activity, configuration, and vulnerability changes.
This requires correlation of security data from vulnerability scanners, SIEM and EDR systems, and cloud security tools.
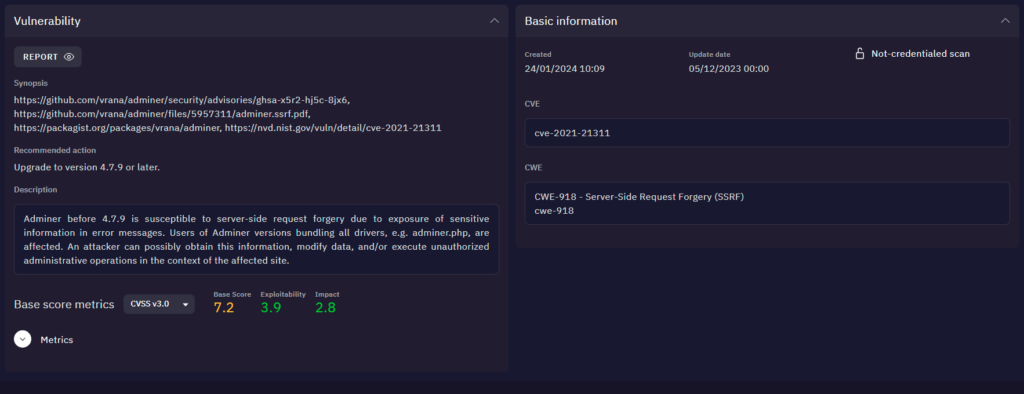
Through its vulnerability management solution, SecureVisio maps vulnerabilities to cyber assets while delivering detailed insights including CVSS scoring, internal risk assessments (evaluating both exploitability and impact), security zone classifications, and extensive contextual data
Identify how threat actors gain initial access to your network and their lateral movements
To identify initial access vectors, you should analyze potential entry points such as web application attack surfaces and cloud service entry points.
Another essential component is analyzing lateral movements, which includes examining authentication mechanisms, network segmentation, and escalation paths (cloud privileges, local privileges, etc.).
You need detailed analysis of access control, including authentication systems and their technical implementations, authorization models, permission inheritance, and privilege escalation opportunities.
Analyze paths, score risks, and remediate
At this point, you have gathered essential information about assets, dependencies, and access vectors to qualify risks for attack paths.
You may employ various techniques for the analysis, including threat modeling, penetration testing, static or dynamic analysis.
Below, we demonstrate a sample modeling output from SecureVisio. Our agent generates a visual representation of your infrastructure (CMDB) and our platform models potential threats and attack paths that threat actors might exploit.
For example, SecureVisio can model user-based attacks targeting your demilitarized zone (DMZ). Our CMDB dynamically generates a graph illustrating potential lateral movement paths and highlighting existing safeguards along these routes.
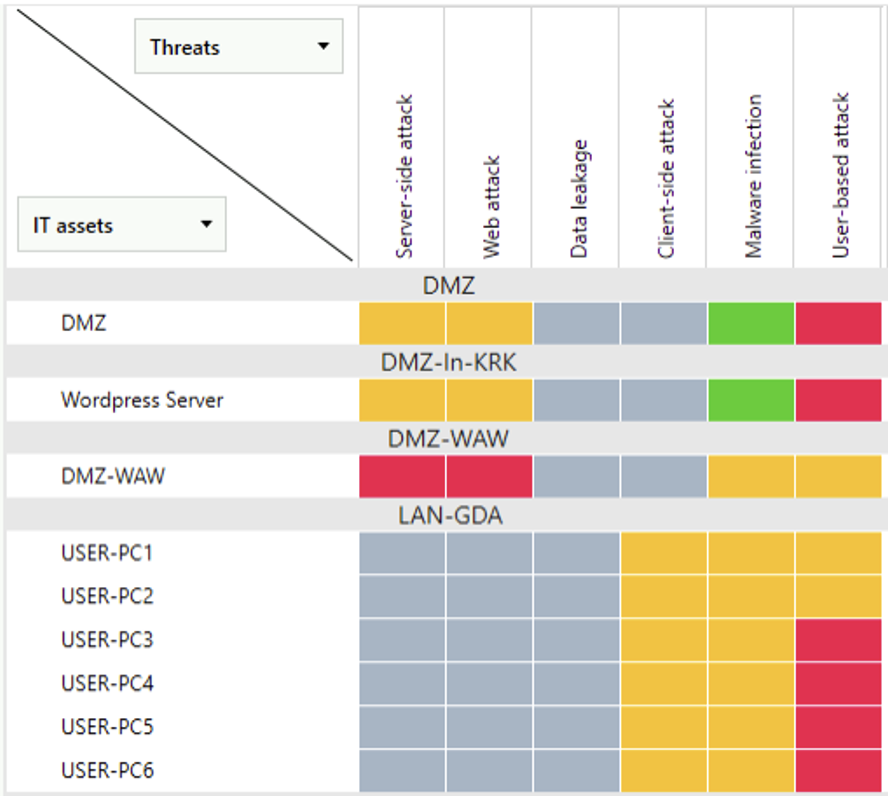
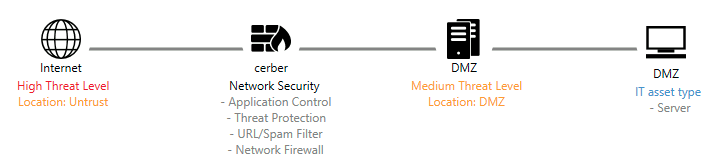
SecureVisio’s powerful correlation engine analyzes CTI feeds, vulnerability scanner output, applied safeguards, business risks, and additional information to provide unique threat intelligence
Our solution delivers detailed insights into existing and recommended safeguards, as well as impacted business processes. Through our drag-and-drop interface, you can easily map business processes (like hosting services) to individual assets, enhancing your risk remediation and incident response decisions.
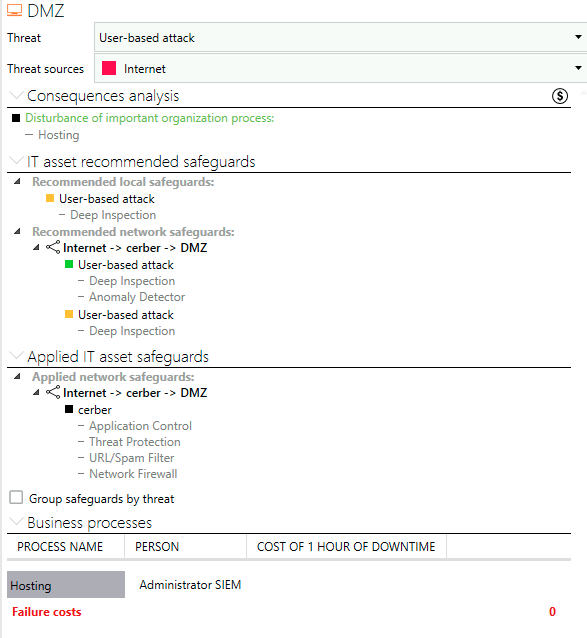
Our risk assessment tool further analyzes risks for specific assets, including attack probabilities, consequence analysis, and safeguard recommendations. Each asset is evaluated for technical feasibility and impact.
All the data collected for threat modeling is then utilized in incident handling.
By providing extensive intelligence on attack paths before they materialize, we help incident handling teams anticipate possible attack scenarios.
Our platform dynamically creates attack paths for events and incidents, allowing teams to understand potential lateral movements.